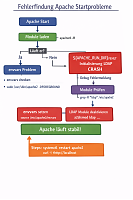
Web statistics anomalies
Datum
Which requests really deserve attention
1. Investigate immediately
Successful responses (status 200, 206, 302) on paths that should not exist:
- /wp-admin/
- /.env
- /.git/config
- /vendor/
2. POST requests without purpose
If your site has no login or upload feature, every POST request deserves scrutiny.
3. Injection attempts
Parameters such as cmd=, ../../ or ${jndi: indicate real exploit attempts.
4. Repeated scans
Many requests from one IP in a short time are usually automated, but worth observing.
5. Unusual HTTP methods
PUT, DELETE or TRACE requests should be noticed – especially TRACE.
6. What you can safely ignore
CMS fingerprint scans, .well-known requests and double slashes are normal internet noise.
Section: What ChatGPT says about this · arteurope / malamadita · free for publication